Dear Reader,
Recently, I’ve observed a noticeable increase in attempts to disable or bypass Windows Defender components — particularly via scripts or misused administrative tools like reg.exe, sc.exe, or even Set-MpPreference. These attempts often target features like:
- Real-time protection
- Tamper Protection
- Defender services or telemetry
The good news? Microsoft Defender for Endpoint (part of the Microsoft XDR suite) does a great job detecting and alerting on such changes. And yes — even simulated attempts can trigger telemetry, as I’ve confirmed in my own controlled test.
MS Defender Tampering Simulation
To validate the detection coverage, I ran a PowerShell simulation script on a test Windows 10 client. The script simply echoed known Defender tampering commands — but in a way that mimics how threat actors often operate, including reg add commands to modify policy keys like:
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection" /v DisableRealtimeMonitoring /t REG_DWORD /d 1 /f
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection" /v UseTPMKey /t REG_DWORD /d 1 /f
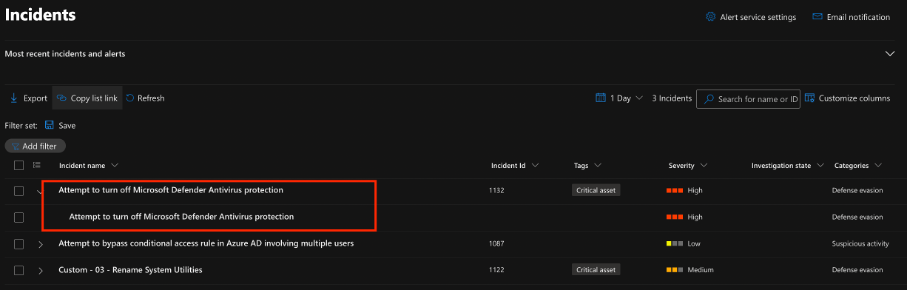
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection" /v UseTPMKeyPIN /t REG_DWORD /d 1 /fWithin a minute, Microsoft Defender XDR picked up the tampering attempts. The results appeared in DeviceProcessEvents, and a correlated Microsoft Sentinel alert was raised.
What is Troubleshooting Mode in Defender?
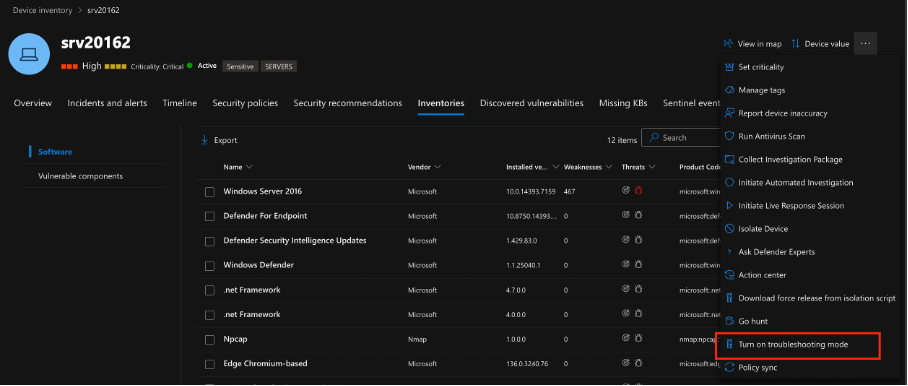
While researching deeper, I explored Defender’s Troubleshooting Mode, which can be enabled manually via:
Enable Troubleshooting Mode – Microsoft Docs
When enabled:
- Tamper Protection is disabled temporarily (default: 4 hours)
- Admins can test and modify Defender settings
- Defender logs this event under AntivirusTroubleshootModeEvent
Activate Troubleshooting Mode:
KQL to Detect Troubleshooting Mode Activation:
DeviceEvents
| where ActionType == "AntivirusTroubleshootModeEvent"
| extend ts_mode = parse_json(AdditionalFields)
| where tostring(ts_mode.TroubleshootingState) == "On"
and tostring(ts_mode.TroubleshootingStateChangeReason) has "started"
| extend
TroubleshootingStarted = todatetime(ts_mode.TroubleshootingStartTime),
TroubleshootingExpiry = todatetime(ts_mode.TroubleshootingStateExpiry),
TroubleshootingDurationMinutes = toint(ts_mode.TroubleshootingStateRemainingMinutes),
StateChangeSource = tostring(ts_mode.TroubleshootingStateChangeSource)
| project
Timestamp, DeviceName, TroubleshootingStarted, TroubleshootingExpiry,
TroubleshootingDurationMinutes, StateChangeSource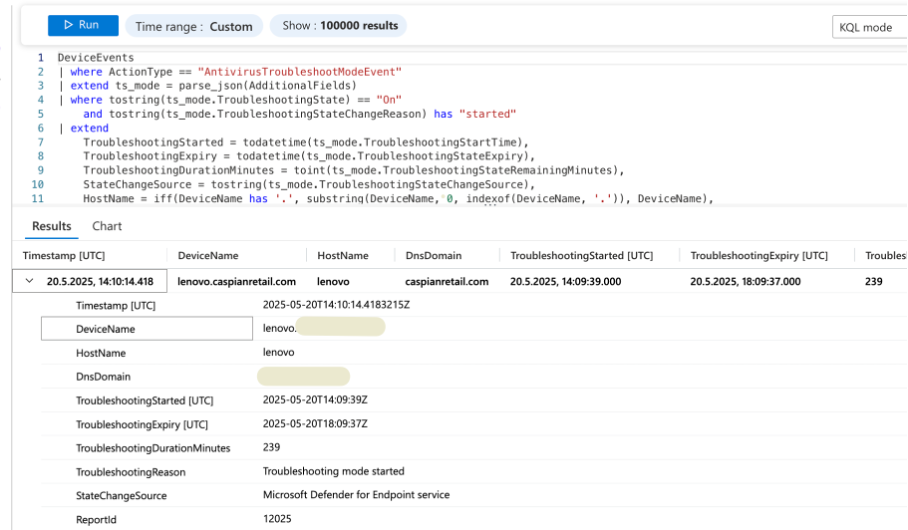
Key Insights
Microsoft Defender for Endpoint reliably logs security-relevant actions like registry changes and configuration attempts. Troubleshooting Mode temporarily disables Tamper Protection, making it a high-visibility event that should be closely monitored. Microsoft Sentinel and KQL provide deep visibility into endpoint behavior, helping SOC teams quickly identify misconfigurations, misuse, or simulated attacks. These detections align with MITRE ATT&CK T1562.001 (Impair Defenses) and are essential for building resilient, alert-driven SOC environments.
This kind of simulation strengthens both detection logic and operational readiness — giving blue teams the tools they need to detect real-world adversary behavior before it leads to escalation.

