In my latest test setup, I focused on capturing and validating Windows Security Event ID 4728, which logs whenever a user is added to a security-enabled global group—a critical action for monitoring privilege escalation.
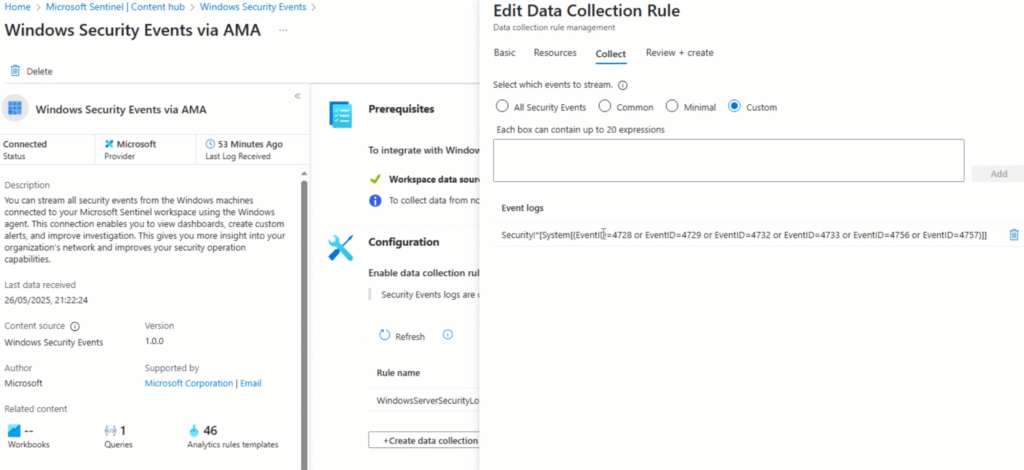
I started by configuring a custom Data Collection Rule (DCR) via Azure Monitor Agent (AMA) to stream only high-value security events (4728, 4729, 4732, 4733, 4756, 4757) to Microsoft Sentinel. This is essential for reducing noise and optimizing data ingestion.
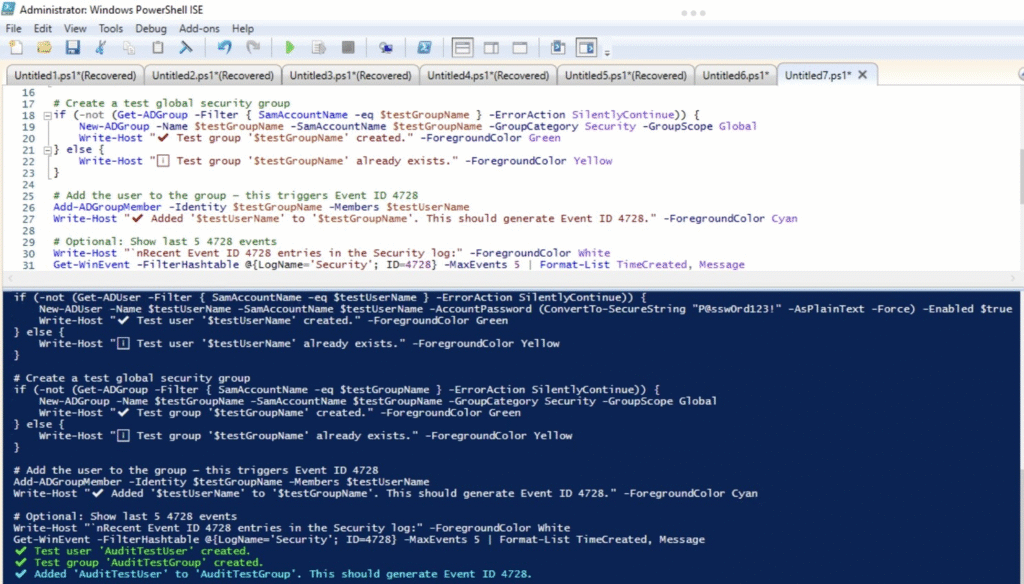
On the domain controller, I simulated the event using PowerShell, by creating a test user and group, then adding the user to the group. As expected, the action triggered Event ID 4728, successfully recorded in the local Security log.
Finally, I verified ingestion into Sentinel and parsed the event with a KQL query using parse_xml() to extract structured fields such as MemberAccount, TargetGroup, and SubjectUserName.
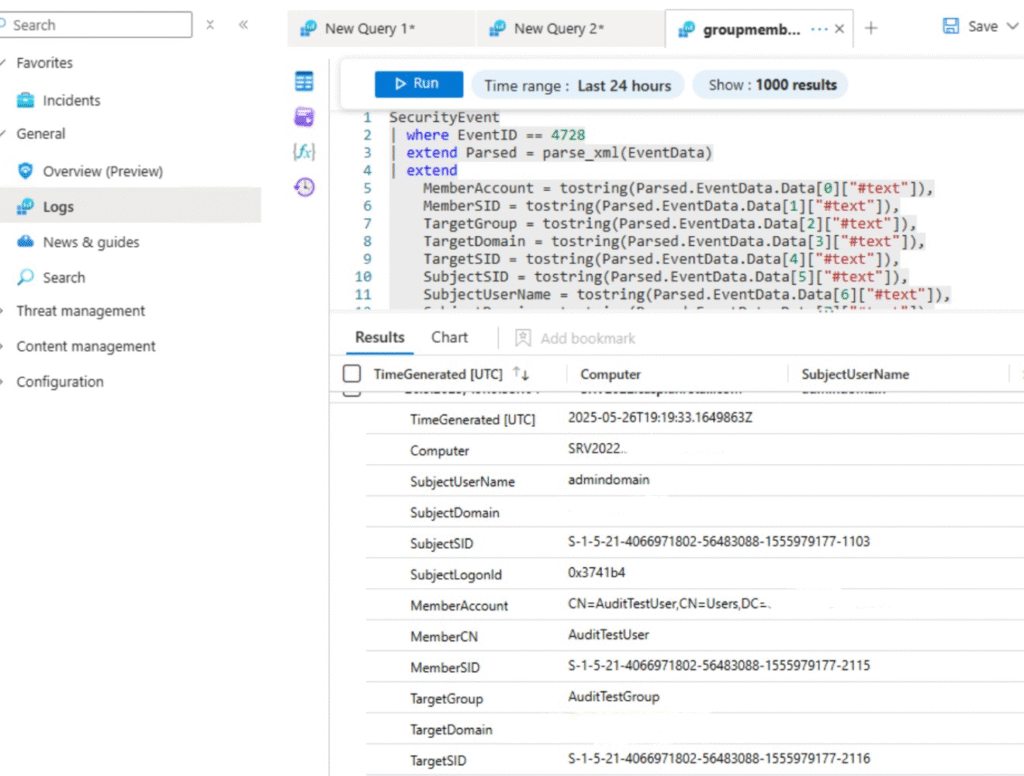
This setup ensures precise detection of privileged group changes, empowering SOC teams to correlate activity, trigger alerts, and investigate lateral movement or insider threats.

